ERP Service Module – Call Handling and Service Orders Control
April 3, 2025
 ERP Service Module – Call Handling and Service Orders Control
ERP Service Module – Call Handling and Service Orders Control
Call Handling Proper operation of a help desk is an essential component of proper servicing and resolution of problems. Service module of an ERP system assists organization to respond promptly both in respect of internal and external customers and gain valuable management data which helps in retaining customers as well as improve internal operation of…
 Why are Companies Constantly Upgrading their ERP Systems?
Why are Companies Constantly Upgrading their ERP Systems?
Enterprise Resource Planning (ERP) is the lifeblood of any business today. Any business, be it a medium scale enterprise or a multinational corporation relies extensively on the use of Enterprise Resource planning systems. This is the reason why these systems tend to be very expensive. There are mega-corporations like SAP and Oracle, which make billions…
 Turbo Charging ERP with BI and CPM
Turbo Charging ERP with BI and CPM
Business Intelligence (BI) – An ERP product provides hundreds of standard reports, generated weekly or monthly or year end basis which acted as a hardcopy dashboards within the organization. In order to improve report generation functionality, an ERP system provides various report writing tools (such as crystal report writer, safari report writer) as well as…
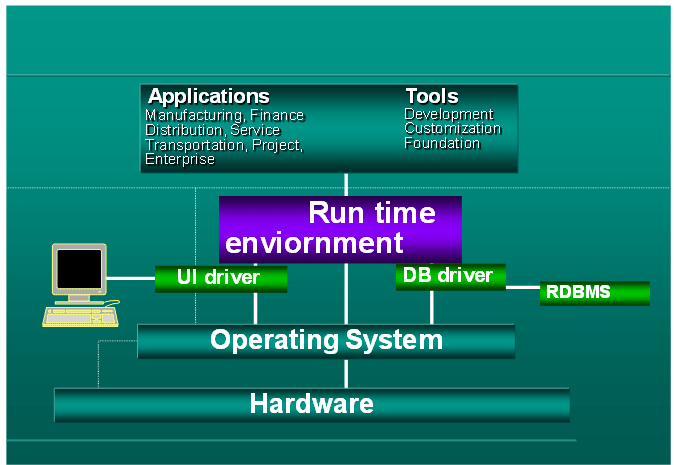
Kernel of an ERP system comprises of a technical module (set of tools) which provides a foundation to various application modules. These tools provide application installation and system administrations functionalities which enables efficient running of applications, within a secured environment. The technical module also provides high level COBOL and 4 GL programming languages (such as ABAP by SAP) which enable application customization and development. The important functions of analytic, report writing, queries, text management and integration with other systems such as office suite are administered through various tools contained in this module. Handling of logs and audit trails of system generated transactions is another functionality which is growing in importance, due to various regulatory requirements such as Sarbanes-Oxley, IFRC and Basel II.
Positioning of Technical modules: In addition to provide a base to various application modules, tools contained in the technical module deal with the hosting environment of the ERP system, namely RDBMS and Operating system. This is clarified in the following diagram:
Installation of an ERP system: The procedure for installation broadly comprises the following:
It may be mentioned that the job of installing an ERP system is done by competent tools experts with the help of detailed installation guides provided by the ERP vendor.
License Management: There are various types of licensing scheme offered by product vendors such as i) named users ii) package based users iii) concurrent users and iv) module based users v) power user (having access to development tools). The license management process is embedded in ERP systems for the purpose of copy protection mechanism and to regulate the commercial use of the system. However, for testing and demonstration purposes, vendors normally provides unprotected software with limited validity, which is needed to be validated and patched before a specified expiration date. The copy protection mechanism is also used by dealers to protect their customizations on the standard ERP software. The license management monitor is implemented by license daemon program.
Validation Process of License: After installation of ERP system under production environment, the software is permitted to be used for a limited period, which is counted from the date of the installation. After this period, the application software is blocked, unless it is validated by product developer.
The validation procedure begins when the requested system configuration is defined by the user immediately after the installation. A report of this configuration and a system generated security key is sent to product developer. Upon receiving the report, validation keys are sent by them which must be entered in the system by the user. The system is then initialized by setting the parameters and is ready for use.
Your email address will not be published. Required fields are marked *