ERP Service Module – Call Handling and Service Orders Control
April 3, 2025
 ERP Service Module – Call Handling and Service Orders Control
ERP Service Module – Call Handling and Service Orders Control
Call Handling Proper operation of a help desk is an essential component of proper servicing and resolution of problems. Service module of an ERP system assists organization to respond promptly both in respect of internal and external customers and gain valuable management data which helps in retaining customers as well as improve internal operation of…
 Why are Companies Constantly Upgrading their ERP Systems?
Why are Companies Constantly Upgrading their ERP Systems?
Enterprise Resource Planning (ERP) is the lifeblood of any business today. Any business, be it a medium scale enterprise or a multinational corporation relies extensively on the use of Enterprise Resource planning systems. This is the reason why these systems tend to be very expensive. There are mega-corporations like SAP and Oracle, which make billions…
 Turbo Charging ERP with BI and CPM
Turbo Charging ERP with BI and CPM
Business Intelligence (BI) – An ERP product provides hundreds of standard reports, generated weekly or monthly or year end basis which acted as a hardcopy dashboards within the organization. In order to improve report generation functionality, an ERP system provides various report writing tools (such as crystal report writer, safari report writer) as well as…
Users interface directly impact usability of an ERP system. A properly designed user interface provides proper accessibility to the intended functions of the system and enables execution of transactions. Earlier users accessed the system with dumb terminals (ASCII) which had lot of usability deficiencies and this led to subsequent adoption of Graphical Users Interface (often with look and feel of MS Windows) during 1990s. With the advent of internet technology, user interface further evolved to enterprise portal, which provides easy access between internet client and application server.
Internet based User Interface: This is the most popular type of users interface at present due to convenience in accessing the ERP applications even from a remote location. Maintenance by system administrator is also easier, as they need not go to individual desktop or use any additional software distribution software, for the purpose of maintenance. The Internet server application is used as a gateway between the Internet client (IC) and the application server in order to expose the ERP functionality to the Internet domain.
The internet user interface architecture is depicted in the following diagram:
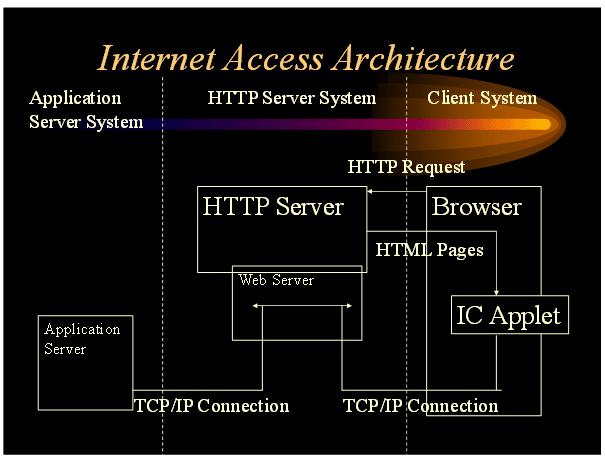
The HTTP-server security mechanisms are used to offer secure access to the HTML-page that contains the Java applet.
User Management: User management functionality is used to create user, provide user login and password and to give authorizations to the users. The user’s authorizations are dependent on their role in a company. To be able to work with ERP applications, users must have some sort of session authorization, database authorization, and library authorization. During installation of ERP, some default roles are automatically created. The default roles make sure that users can use the menu browser and its associated functions and commands.
Users Type: There are various types of users for an ERP package which can be broadly classified as under:
Role dependent users’ authorization: From a user point of view, a role represents a function in an organization. In ERP, a role represents a set of authorizations for a function in a company (database). User authorizations that are defined per role instead of per user significantly reduce the redundant data. The authorizations for normal users are therefore defined in roles to which they can be linked. The role concept provides a user-friendly method to quickly add new users or to update user authorizations.
Because an employee can have more than one function in a company, more than one role may be assigned to the user. A role can also contain more than one sub-role, which can also have sub-roles. All these roles and sub-roles form a role tree, which can be viewed with a role browser. The role browser shows the role tree in a graphical user interface.
Role-dependent authorizations can be defined at the following component levels in an ERP system:
The non-role-dependent authorizations: In addition to these role-dependent authorizations, some additional authorizations can be specified that are not defined by the employee’s role, for example, the development parameters, device preferences, and so on. These non-role-dependent authorizations are defined in templates to reduce redundant data, which then can be linked to the user profile.
These templates pertaining to non role dependent authorization can be divided into the following categories:
Your email address will not be published. Required fields are marked *